The Daily Raptor
Newsletter Signup: dailyraptor.com
Tuesday, July 22, 2025 Edition
Mentioned in this edition:
Kelly Jones, CPO Cisco Systems / Abnormal Security / CertifID / Business Email Compromise / Wire Fraud / Cybersecurity Poverty Line
Cybersecurity Poverty Line to the Front Lines of Fraud

In last week’s Daily Raptor feature, “Surviving Below the Cybersecurity Poverty Line,” we explored the widening digital divide between organizations with well-funded security operations and those operating with minimal protections. But the real insight came from Kelly Jones, Chief People Officer at Cisco, who reminded us:
“In many of the toughest cybersecurity moments, the hero is the human.”
-Kelly Jones, Chief People Officer at Cisco
That wisdom is especially urgent when it comes to Business Email Compromise (BEC)—a threat category that exploits both digital weaknesses and human vulnerability. For organizations below the cybersecurity poverty line—like title companies, real estate firms, family law practices, doctor’s offices, and M&A attorneys—a single misstep can be financially devastating. Many of these small offices manage tens of millions in transactions each month, yet rely on email chains, outdated processes, and well-meaning but untrained personnel to guard the digital gate.
According to CertifID’s State of Wire Fraud 2025, BEC attacks targeting real estate transactions now account for nearly $500 million in annual losses. These organizations operate in fragmented regulatory environments, handle ultra-high-value transactions, and lack uniform IT infrastructure—making them ideal targets for cybercriminals.
Business Email Compromise: More Than a Tactic—An Entire Threat Category
BEC isn’t just a subset of phishing. It’s a multi-billion-dollar criminal model built on trust manipulation, timing, and precision impersonation—and increasingly, on artificial intelligence.
At its core, BEC uses highly personalized messages (often appearing to come from known contacts or authorities) to trick employees or clients into altering wire instructions, approving fake invoices, or leaking sensitive information.
At its core, this is a human problem—exploiting trust, stress, and oversight under pressure::
Over 1 in 4 homebuyers or sellers report receiving suspicious communications during their closing process
Nearly 1 in 20 fall victim to fraud (source: CertifID)
Victims are often first-time buyers, overwhelmed clients, or solo administrators managing multiple transactions on tight timelines.
And now, we’ve entered a new chapter: the AI-augmented BEC era.
Fraudsters are using generative AI to:
Create authentic-looking emails
Clone voices of agents or attorneys
Generate real-time deepfake video calls
In one 2025 incident, a finance employee transferred $25 million after joining a video call with an AI-generated fake CFO.
The Business Email Compromise Crisis: What Every Business Executive Should Know
Summary:
Soft targets handle trillions in transactions with minimal security budgets
Organizations moving >$10M annually with <$100K in security spend are prime targets
Average BEC loss for under-protected organizations: $1.2M per incident
AI-powered attacks are actively hunting high-value soft targets
Time to implement protection: 90 days
Cost: ~0.1% of transaction volume
Risk reduction potential: Up to 95% with targeted defenses
The Perfect Storm: Maximum Value, Minimal Defense
Your organization moves $50 million monthly via wire transfers—but your email security hasn’t been updated since 2019. You’re not alone.
Across America, sectors moving trillions—many in real estate, healthcare, manufacturing, legal—operate with cybersecurity budgets that wouldn’t protect a retail store.
Real-world examples:
A small law firm managing a $280M acquisition lost $3.7M to BEC. Annual security budget: $15K
A regional healthcare network processing $500M in claims discovered 6 months of diverted payments. IT security: one part-time contractor
A family-owned manufacturing supplier lost $4.2M in one afternoon. Security: a single endpoint tool and “good intentions”
The Soft Target Economy: Where Billions Meet Basic Defenses
Sector Vulnerabilities:
Real Estate: $2.5T annually; 29% of title companies spend <$1K/year on security
Midsized healthcare: $4.3T in transactions, often reliant on outdated email systems
Modest-sized manufacturing: Billions in supply chain value, often no dedicated security staff
Legal/M&A: High-stakes deals via consumer-grade email
Shared Risk Characteristics:
Massive transaction volumes
Legacy technology
Fragmented oversight
Publicly visible transaction data
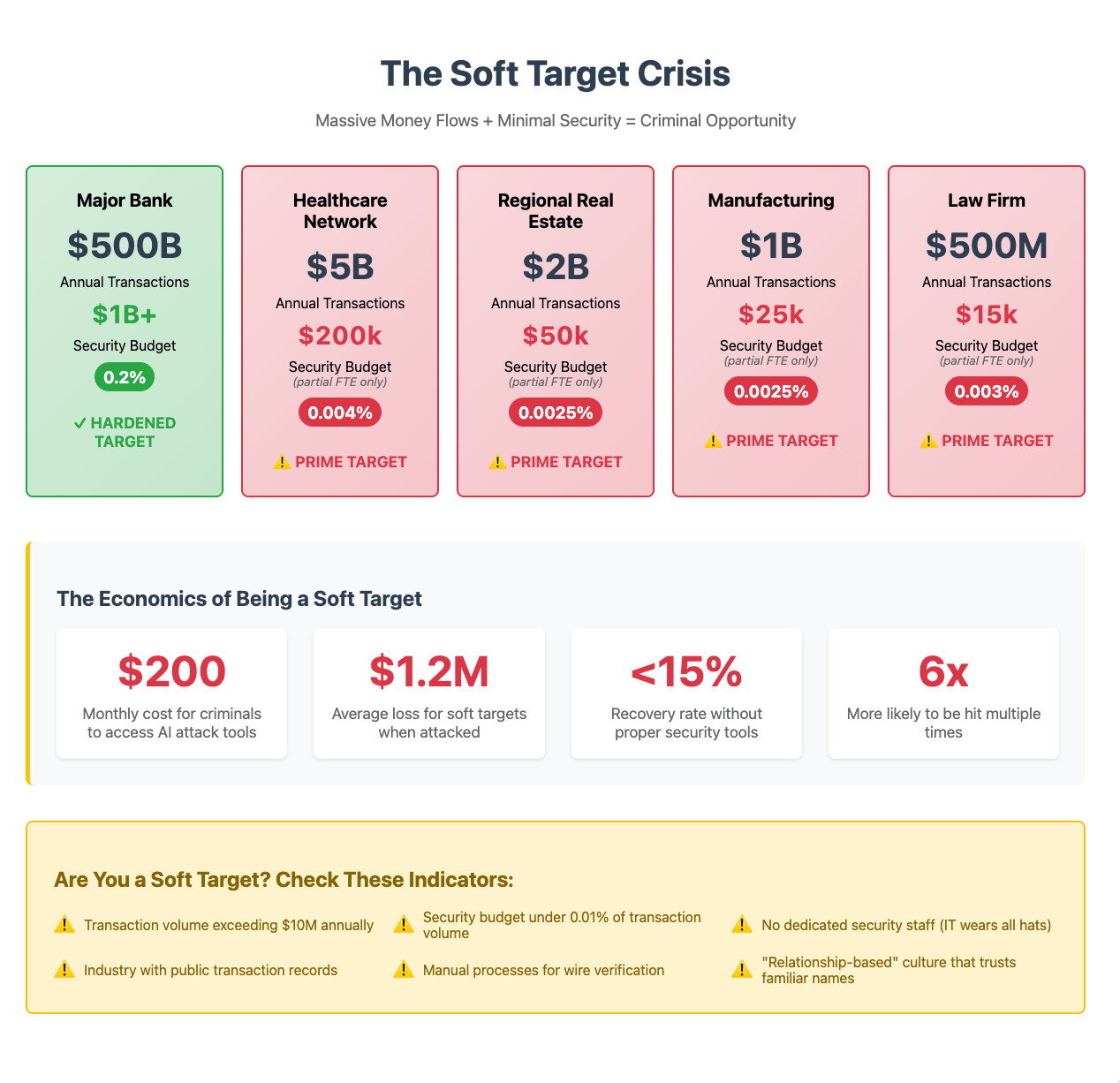
The Resource Gap Criminals Exploit
Sector | Annual Transaction Volume | Typical Security Budget | Security as % of Volume | Attractive to Attackers? |
|---|---|---|---|---|
Major Bank | $500B | $1B+ | 0.2% | Hardened target |
Regional Real Estate | $2B | $50K | 0.0025% | Prime target |
Healthcare Network | $5B | $200K | 0.004% | Prime target |
Mid-size Manufacturing | $1B | $25K | 0.0025% | Prime target |
Law Firm | $500M | $15K | 0.003% | Prime target |
Why AI Makes Soft Targets Softer
AI doesn't need to breach fortified walls—it finds unlocked doors.
Automated Targeting: Scans public records, identifies valuable targets
Scalable Exploits: Crafts convincing messages in minutes
Team Overload: Outpaces small teams with rapidly mutating attacks
Malicious GPTs: Tools like WormGPT and FraudGPT enable scalable attacks
Low Cost of Entry: $200/month buys powerful AI tools—no hacker degree required
Soft Target Indicators
You're likely a prime target if:
You move >$10M annually
Your security budget is <0.01% of transaction volume
You have no dedicated security staff
You operate in sectors with public transaction records
Your team gets overwhelmed by seasonal spikes
Your culture is relationship-based and trust-driven
Wire verification is manual or inconsistent
There’s no formal security training or simulations
Real-World Carnage: When Soft Targets Get Hit
Case Study: Regional Title Company
Volume: $2.8B/year
Security Budget: $45K
Loss: $4.7M in 48 hours
Aftermath: Shuttered, 47 layoffs, lawsuits
Case Study: Healthcare Processor
Volume: $950M/year
Security Budget: "Whatever IT can squeeze in"
Loss: $8.3M over 6 months
Aftermath: Under federal investigation, CEO resigned
Case Study: Manufacturing Supplier
Volume: $375M/year
Security Budget: $22K
Loss: $2.1M via deepfake video call
Aftermath: Lost 3 major contracts, 20% workforce reduction
The Soft Target Tax: The True Cost of Underprotection
Average BEC loss: $1.2M (for orgs with <$100K security budget)
Recovery rate: <15% without security tools
Time to detect fraud: 73 days (without monitoring)
Repeat attacks: 6x more likely for soft targets
Secondary costs: 3–5x initial loss (legal, trust, reputation)
The Ripple Effects of Soft Target Breaches
When a title company loses $500K, it’s not just their loss. It’s:
A family’s home
A retiree’s life savings
A business’s growth capital
Ripple effects include:
Delayed deals across sectors
Frozen capital
Higher premiums
Collapsing trust
Job loss and industry-wide skepticism
The Realistic 90-Day Plan for Soft Targets
Days 1–30: Triage & Assess
Identify highest-risk transactions
Flag employees handling >$1M transactions
Document wire transfer processes
Calculate soft target score = Transaction Volume ÷ Security Spend
Days 31–60: Targeted Hardening
Deploy AI-driven email security
Enforce mandatory callbacks for (>$10K?) wires
Create “transaction security zones”
Partner with a cybersecurity firm that knows your sector
Days 61–90: Scale Smart
Prioritize protection by transaction value
Train teams using real attack simulations
Build relationships with law enforcement
Create incident response playbooks (BEC, ransomware, wiper attacks)
Consult a partner for industry-specific strategy and tools
Consider insurance coverage, particularly large transactions
The Path Toward a Smart Defense
You don’t need Fortune 500 resources to stop being a soft target.
But you do need to act—because criminals are already acting on you.
The math is simple:
Your annual volume: $100M+
Your security budget: <$100K
Their monthly investment: $200 for AI tools
Their potential gain: $1M–$5M per attack
The question isn’t “Can we afford protection?”—
It’s “Can we afford to stay the weakest link in a trillion-dollar chain?”
The time to act is now—no one wants to be the next case study.
For immediate soft target assessments and industry-specific protection, contact a capable cybersecurity provider who understands (deeply) your risk profile.
Stay cool this week, Raptor Community.
— The DR Team
/smb
Newsletter Signup: dailyraptor.com
An imPAWster revealed…
- The below attachments helped to inform this publication:
/

![[WHITEPAPER] State of Wire Fraud 2025 _ CertifID.pdf](https://media.beehiiv.com/cdn-cgi/image/fit=scale-down,format=auto,onerror=redirect,quality=80/static_assets/file_attachment.png)