The Daily Raptor
Newsletter Signup: dailyraptor.com
Friday, July 31, 2025 Edition
China, Inside The Wire: Part III
Sector-by-Sector Infrastructure Siege
Last week, we exposed China's cyber playbook for seizing Taiwan: a 72-hour blitz where U.S. civilian cyber infrastructure—not military bases—is the first target. We made it plain: America's power grids, ports, and payment systems aren't just collateral—they are the battlefield. This isn't an obscure future threat. It's a live-wire reality.
Today, we go deeper. If Volt/Salt Typhoons are a match, America's critical infrastructure is the dry kindling - or so the adversary is hoping.

In Part 3 of our series, we unpack how the kill chain plays out across six foundational infrastructure sectors—energy, communications, finance, transportation, water, and healthcare. You'll see real threat actor patterns, the People's Liberation Army (PLA) doctrine in action, and how tech/software supply chain compromises remain a top-tier risk. This isn't just about preparation—it's about resilience & survival. Whether you're a CISO, CIO, or vendor partner, understanding the sector-specific battlefield is now a strategic imperative.
The Siege & Kill Chain by Sector
China's Typhoon Forces: A Coordinated Infrastructure Campaign
The People's Republic of China (PRC) hasn't deployed just one cyber unit—it's unleashed a typhoon season. While Volt Typhoon grabs headlines for pre-positioning in power grids and water systems, it's part of a larger coordinated campaign:
Volt Typhoon (2019-present): Embedded in energy, water, transportation—ready to pull the plug
Salt Typhoon (2020-present): Compromising major U.S. telcos, potentially accessing call records and communications
Flax Typhoon: Building botnets from compromised IoT devices for distributed attacks
Brass Typhoon: Targeting government and NGO networks
This isn't random activity—it's synchronized preparation. Salt Typhoon's telecom access provides intelligence for Volt's targeting. Flax's botnets offer attack infrastructure. Each group maintains plausible deniability while advancing Beijing's strategy: own the infrastructure before the conflict begins.
Their reach spans both the continental U.S. and territories like Guam, with sector-specific activity profiles:
Energy: Persistent mapping of industrial control systems (ICS) and SCADA networks
Finance: Sophisticated data exfiltration campaigns targeting transaction systems
Healthcare: Ransomware precursor activity and theft of medical research IP
Water systems: Reconnaissance of operational technology that could disrupt purification processes
Transportation: Network reconnaissance and access development across aviation, rail, and maritime sectors to disrupt logistics and troop movement in crisis scenarios
Communications: Targeting of telecom infrastructure and satellite systems to degrade command, control, and public communications in conflict
The Kill Chain Mechanics: PLA/MSS Recon to Readiness
The People's Liberation Army (PLA), in partnership with the Ministry of State Security (MSS) has developed cyber playbooks that go far beyond espionage. The PRC's goal is not just surveillance—it's to create disruptive and destructive effects during the early and ongoing stages of conflict.
Within this highly orchestrated activity, the kill chain unfolds with methodical precision:
Reconnaissance: PRC operators spend months mapping your infrastructure—every PLC in your water treatment plant, every relay in your power grid, every core router in your telecom network. They document firmware versions, identify unpatched systems, and catalog emergency shutdown procedures.
Weaponization: Custom malware is crafted for your specific infrastructure. They're not using off-the-shelf tools—they're building exploits for your exact Siemens S7-1200 PLCs or your ABB relay protection systems (as examples).
Delivery: Access comes through multiple vectors—compromised VPNs, supply chain implants in software updates, or hijacked MSP credentials. They prioritize "living-off-the-land" techniques, using legitimate tools like PowerShell and WMI to blend with normal traffic.
Exploitation: Initial compromise targets high-value nodes—domain controllers, industrial DMZs, SCADA jump boxes. One foothold becomes ten, then a hundred, as they move laterally using stolen credentials.
Installation: This is where patience pays off. They embed kernel-level rootkits, firmware implants, and modified device drivers that persist through reboots and rebuilds. Some implants have been dormant for years.
Command & Control: Encrypted communications hide in legitimate traffic—HTTPS to compromised web servers, DNS tunneling, even steganography in image files. Multiple redundant channels ensure they maintain access.
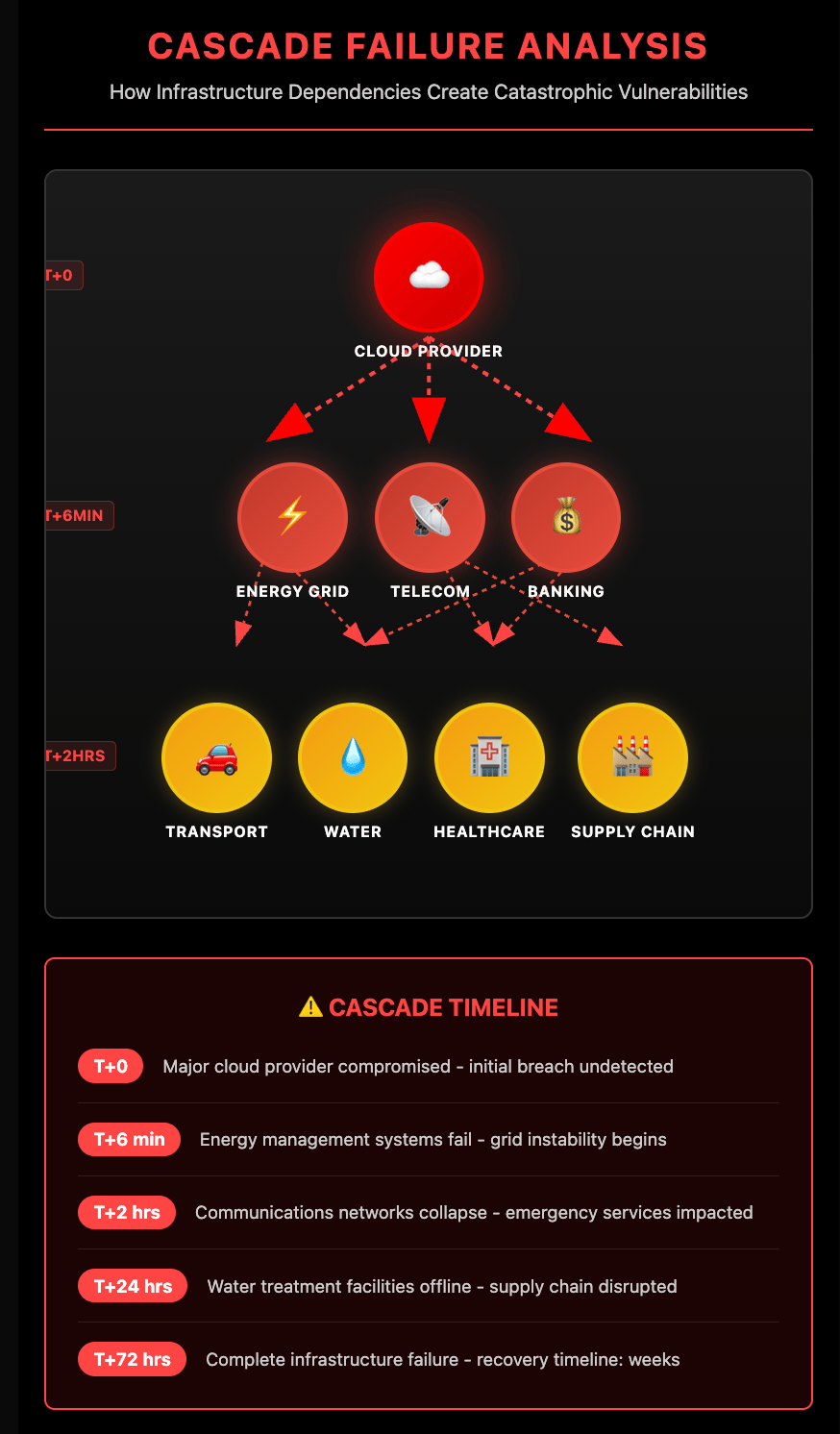
Actions on Objectives: The payloads wait. When activated, they won't just encrypt data or steal files—they'll open dam spillways, corrupt power generation signals, or inject false data into financial systems. Simultaneous activation across sectors creates cascading failures that compound the damage.
This isn't theoretical—it's their operational doctrine, refined through years of patient preparation.

The Typhoon Constellation
Salt Typhoon (2020+): Major U.S. telecom compromise for intelligence gathering Volt Typhoon (2019+): Pre-positioned for infrastructure disruption
Flax Typhoon: IoT botnet operations
Brass Typhoon: Targeting government and NGO networks
Why it matters: Coordinated groups = coordinated attacks. Defense requires understanding the full battlefield.
Future Outlook: A Threat Timeline to 2035
Looking ahead, the risk profile intensifies as U.S.-PRC tensions potentially escalate over Taiwan and other flashpoints.
By 2027, the PLA's military modernization milestone, expect these coordinated cyber forces to execute synchronized, multi-sector attacks—with telecom disruption preventing response coordination while infrastructure fails in cascade.
By 2035, coordinated disruption across infrastructure sectors may serve as a strategic first strike, undermining public confidence and delaying U.S. military response.
These operations are evolving from reconnaissance and access development toward operational readiness—designed for pre-conflict execution or "left of boom" actions.
Immediate Steps for Infrastructure Defenders
To counter these threats, CIOs, CISOs, and technology vendors must move from reactive to anticipatory defense. That means:
Implement robust segmentation between IT and OT networks
Deploy deception technologies to detect dormant adversaries
Establish sector-specific threat intelligence sharing to link indicators across domains
Develop degradation-tolerant architectures to maintain core functions during compromise
Diversify supply chains and tech stacks to reduce systemic dependency
Assume compromised communications: Plan response coordination with degraded telecom infrastructure
Cross-reference threat intelligence: Link indicators across Volt, Salt, Flax, and other PRC groups
Vendor Security is National Security
Software vendors are no longer peripheral—they are the front line.
A compromised software build can move laterally across thousands of customers within minutes. To defend at this scale, vendors must adopt "assume breach" postures and implement structural reforms in how software is built and delivered.
Key priorities include:
Cryptographic signing of all code releases with hardware security modules
Continuous behavioral monitoring of development environments
Clean room rebuilds of build infrastructure
Participation in coordinated vulnerability disclosure (CVD) programs
Adoption of Software Bills of Materials (SBOMs) and reproducible builds
SBOMs, in particular, serve as critical assets. Like an "ingredients list," they enable security teams to instantly identify whether a compromised open-source component exists in downstream applications—facilitating rapid exposure analysis during a cascading compromise event.
Quick Hits
Infrastructure is the battlefield: All six core sectors now face persistent prepositioning by state-backed threat actors.
It's not one group, it's a campaign: Volt Typhoon is one storm in China's typhoon season—Salt targets comms, Flax builds botnets, each enabling the others.
Volt/Salt/Flax/Brass Typhoons: Already embedded: Active since 2019+, their objective is disruption at scale—not surveillance.
From recon to readiness: PLA kill chains are transitioning from mapping to operational execution ahead of 2027.
Supply chains as attack surfaces: Software vendors and MSPs remain high-leverage entry points across multiple sectors.
SBOMs as strategic assets: Software Bills of Materials are now essential for rapid exposure analysis during cascading compromises.
Assume breach, Build-In Resilience: Sector leaders must adopt architectures tolerant to partial system failure and degraded operations.
Vendors are critical infrastructure: Development environments require the same protection as national assets.
Left of Boom (T- “x” Conflict) is now: China's cyber posture anticipates infrastructure disruption before kinetic action—a shift that demands immediate executive focus.
The Hard Truth
America's infrastructure doesn't fail in theory—it fails in layers. And China knows exactly which threads to pull.
And it's not just infrastructure they've mapped—Salt Typhoon's telecom compromise means they're potentially listening to how we'd coordinate our response. When the lights go out, comms/phones might be compromised too.
Our systems were designed for efficiency, not resilience. In a contested environment, a single compromised software update can ripple across six sectors in six minutes.
That's not hypothetical—it's operational doctrine.
If you're a CIO or CISO, your plan can't assume the lights stay on. If you're a vendor, your product is a battlefield. If you're waiting for more evidence, understand this: The breach isn't coming—it was silently versioned, compiled, and shipped years ago.
They've Mapped Every Dependency. Have You?
The only question now is whether we'll disrupt their plan—or be consumed by it.
This Raptor Community lives where defense begins—Left of Boom. Let’s mobilize, operationalize & work together to keep it that way.
The DR Team /smb
Want The Entire Daily Raptor Early? Email Newsletter Signup: dailyraptor.com
Resource Note: We'll arm you with the intelligence you need—resources, analysis, and evidence dropping weekly as we expose each layer of this threat
Recommended Reading that helped to inform this series:
The Hundred Year Marathon, Michael Pillsbury
Superpower Showdown, Ling Ling Wei
Spies, Lies, and Algorithms: The History and Future of American Intelligence, Amy Zegart, Stanford University

